By Urs Fischer, eidg. dipl. Wirtschaftsprüfer, CRISC, CISA, Fischer IT GRC Beratung & Schulung
IT risk» as defined by the «Risk IT Framework», is the business risk associated with the use, ownership, operation, involvement, influence and adoption of IT within an enterprise.
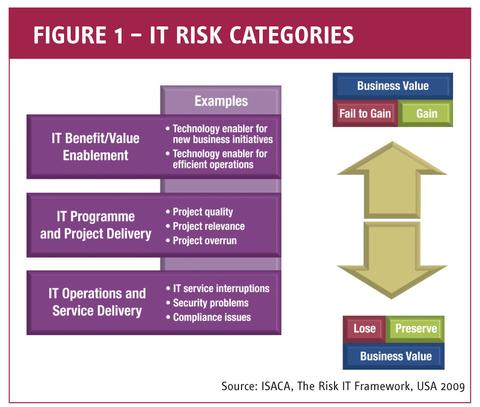
IT risk consists of IT-related events that could potentially impact the business. It is characterised by both uncertain frequency and magnitude, and it creates challenges in meeting strategic goals and objectives as well as uncertainty in the pursuit of opportunities. IT risk can be categorised as (refer to Figure 1):
- IT service delivery risk, which is associated with the performance and availability of IT services
- IT solution delivery/benefit realisation risk, which is associated with the contribution of IT to new or improved business solutions, usually in the form of projects and programmes
- IT benefit realisation risk, which is associated with (missed) opportunities to use technology to improve efficiency or effectiveness of business processes, or to use technology as an enabler for new business initiatives – IT risk always exists, whether or not it is detected or recognised by an organisation.
Figure 1 – IT Risk Categories
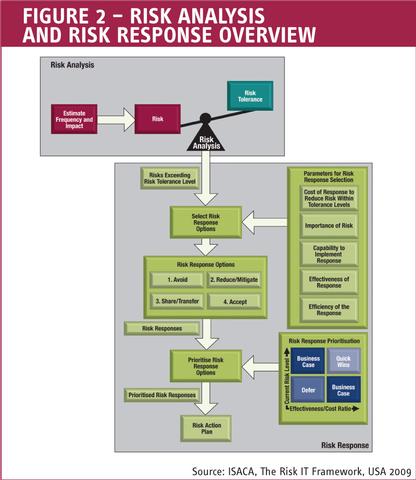
Figure 2 – Risk Analysis and Risk Response Overview
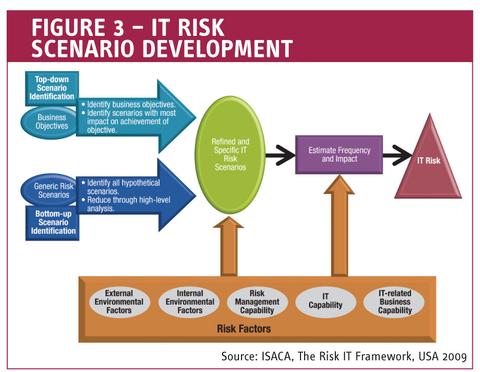
Figure 3 – IT Risk Scenario Development
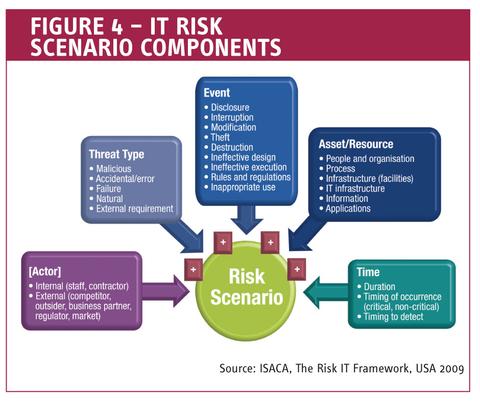
Figure 4 – IT Risk Scenario Components
IT Risk Management Objectives
As risk management is a pervasive and strategic requirement in any enterprise, the main objectives of an IT Risk Management Framework are to enable users to:
- Integrate the management of IT risk into the overall enterprise risk management of the organisation
- Make well-informed decisions about the extent of the risk, the risk appetite and the risk tolerance of the enterprise
- Understand how to respond to the risk
In summary, Risk Management allows an enterprise to make appropriate risk-adjusted decisions.
Benefits
A Risk Management Framework addresses many issues enterprises face today, notably their need for:
- An accurate view of current and near-future IT-related risks throughout the extended enterprise and the success with which the enterprise is addressing IT risk
- End-to-end guidance on how to manage IT-related risks, beyond both purely technical control measures and security
- Understanding of how to capitalise on an investment made in an IT internal control system already in place to manage IT-related risk
- When assessing and managing IT risk, integration with the overall risk and compliance structures within the enterprise
- A common framework/language to help manage the relationship amongst executive decision makers (board/senior management), the chief information officer (CIO) and enterprise risk management, or between auditors and management
- Promotion of risk responsibility and its acceptance throughout the enterprise
- A complete risk profile to better understand risk, so as to better utilise company resources
IT Risk Management Principles
Guiding principles for effective management of IT risk should be based on generally accepted enterprise risk management principles (COSO, ISO31000 etc.), which should be applied to the domain of IT. ISACA’s Risk IT process model is designed and structured to enable enterprises to apply the principles in practice and to benchmark their performance. The principles are split in a governance part and a management part:
- Effective enterprise governance of IT risk:
> Always connects to business objectives
> Aligns the management of IT-related business risk with overall enterprise risk management
> Balances the costs and benefits of managing risk
- Effective management of IT risk:
> Promotes fair and open communication of IT risk
> Establishes the right tone from the top while defining and enforcing personal accountability for operating within acceptable and well-defined tolerance levels
> Is a continuous process and part of daily activities
IT Scenario Analysis in Enterprise Risk Management
One of the challenges for IT risk management is to identify the important and relevant risks that can possibly occur with IT or in relation to IT, given the pervasive presence of IT and the business dependence on it. One of the techniques to overcome this challenge is to develop and use risk scenarios. Scenarios are a powerful tool in a risk manager’s armory—they help professionals ask the right questions and prepare for the unexpected. Scenario analysis has become a «new» and best practice in enterprise risk management (ERM). Scenario analysis is also a centrepiece of ISACA’s Risk IT framework.
It is a core approach to bring realism, insight, organisational engagement, improved analysis and structure to the complex matter of IT risk. Once these scenarios are developed, they are used during the risk analysis, where frequency of the scenario actually happening and business impacts are estimated. This is shown in Figure 2.
Risk scenario analysis is a technique to make IT risk more concrete and tangible and to allow for proper risk analysis and assessment . It is a core approach to bring realism, insight, organizational engagement, improved analysis and structure to the complex matter of IT risk. The risk scenario is structured as follows:
- Description of the scenario analysis flow, showing the importance and relevance of risk scenarios
- Discussion of risk factors that need to be taken into account when creating and assessing risk scenarios
- Explanation of the different components in a risk scenario
- Guidelines on how to construct a set of relevant risk scenarios
Once these scenarios are developed, they are used during the risk analysis, where frequency of the scenario occurring and business impacts are estimated.2)
Figure 3 shows that IT risk scenarios can be derived by two different ways:
- A Top-Down Approach, where one starts from the overall business objectives and performs an analysis of the most relevant and probable IT risk scenarios impacting the business objectives
- A Bottom-Up Approach, where a list of generic scenarios is used to define a set of more concrete and customized scenarios
The approaches are complementary and should be used simultaneously. Indeed, risk scenarios must be relevant and linked to real business risk. On the other hand, using a set of example generic risk scenarios helps to ensure that no risks are overlooked and provides a more comprehensive and complete view of IT risk.
The following is a practical approach that proved very helpful in developing a set of relevant and important risk scenarios:
1. Use a list of example generic risk scenarios to define a manageable set of concrete risk scenarios for the organization
2. Perform a validation against the business objectives of the organization
3. Refine the selected scenarios based on the validation; categorize them to a level in line with the criticality of the organization
4. Reduce the number of scenarios to a manageable set
5. Keep all risks in a list so they can be re-evaluated in the next iteration and included for detailed analysis if they have become relevant at that time
6. Include in the scenarios an unspecified event; how to address an incident not covered by other scenarios
An IT risk scenario is a description of an IT-related event that can lead to a business impact, when and if it should occur. For risk scenarios to be complete and usable for risk analysis purposes, they should contain the components as shown in Figure 4.
Scenario Analysis is not rocket science. But why don’t organizations use it more often and routinely? Keep in mind, that scenarios are in fact harder to develop as it seems. A good one takes time to build, and so a whole set takes a large investment of time and energy.
Conclusion
The Risk IT Framework and The Risk IT Practitioner Guide are designed to allow business managers to identify and assess IT-related business risks and manage them effectively. It provides the missing link between enterprise risk management (ERM) and IT risk management and control, fitting in the overall IT Governance Framework of
ISACA, and building upon all existing risk-related components within the current frameworks of CobiT and Val IT.
More information
For more information on Risk IT, please visit
www.isaca.org/riskit. The publications are available in the
ISACA Bookstore, www.isaca.org/bookstore. The Risk IT Framework is available as a complimentary PDF for ISACA members and nonmembers at
www.isaca.org/downloads. The Risk IT Practitioner Guide and tool kit are available as complimentary downloads for ISACA members at www.isaca.org/downloads.
1) Based on ISACA’s research publications «Risk IT Framework» and «Risk IT Practitioner Guide», published 2009
2) Risk Analysis and Risk Assessment – Risk Analysis is the actual estimation of frequency and magnitude/impact of a risk scenario. Risk Assessment is a slightly broader term, including the preliminary and ancillary activities around risk analysis, i.e., identification of detailed risk scenarios and definition of responses.
Der Autor
Urs Fischer, eidg. dipl. Wirtschaftsprüfer, CRISC, CISA ist unabhängiger Berater und Anbieter von Schulungen im Bereich IT Governance, Risiko Management und Compliance. Als Leiter IT Governance & Risiko Management bei einer grossen Schweizer Lebensversicherung implementierte er ein effektives und effizientes IT Risiko Management- und Kontroll-Framework. Seit 1989 arbeitet er im Bereich IT Governance, Revision und Sicherheit und hat während dieser Zeit umfassende Erfahrung in IT Governance, Risiko Management, Internen Kontroll-Systemen und Informationssicherheit sammeln können.
Urs Fischer ist sehr aktiv in der IT Kontroll- und Sicherheits-Gemeinde. Er war wesentlich beteiligt an der Entwicklung von ISACA’s Kontroll-Framework COBIT 4.1 und ist auch in die Weiterentwicklung von COBIT5 involviert. Als Vorsitzender von ISACA’s Risk IT Taskforce war er federführend in der Entwicklung des «Risk IT Frameworks» und des «Risk IT Practitioner Guide» involviert. Als Dank für seine Beiträge zugunsten des Berufsstandes wurde ihm 2010 der «John W. Lainhart IV – Common Body of Knowledge Award» verliehen.